Published on
As technology advances, so do the potential threats to application security. In order to protect your organization's applications from attack, it is essential to have a strong foundation in the three pillars of application security: process, technology, and people.
Each pillar plays an equally important role in ensuring the security of your applications.
In this article, we will dive into each pillar and provide actionable steps to help you implement measures to support all three pillars and protect your applications from potential threats.
AppSec Pillar #1: Process
The processes pillar refers to the policies, procedures, and workflows used to manage applications. These processes should be designed to minimize risk and ensure that applications are secure throughout their lifecycle.
Let's review how you can support the Process Pillar of Application Security:
Adopt 'Shift Left' For Your SDLC
According to 2023 EMA Research, 69.3% of organizations have SDLCs that miss critical security steps.
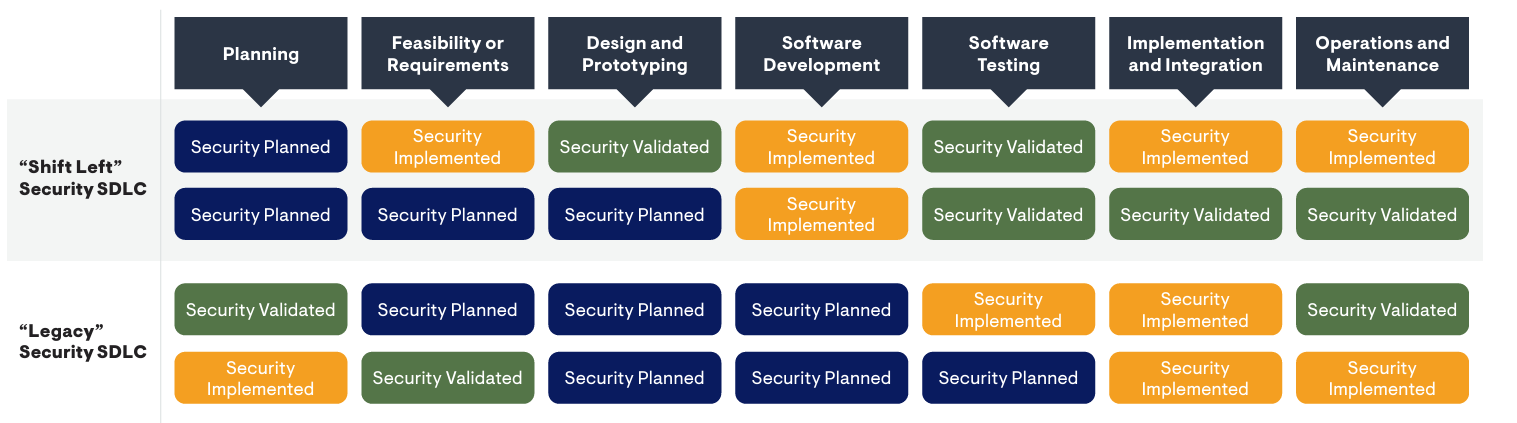
The Shift Left Movement is dedicated to improving how organizations approach security testing and vulnerability management. Instead of leaving security until the end, the movement's goal is to "shift security left" into earlier phases of the development timeline.
Let's look at an example of shift left when for SDLC:
Free Download: Secure Coding Practices – Growing Success or Zero-Day Epidemic?
Address Security Concerns Early in the Development Process
Security concerns should be addressed early in the development process, rather than waiting until testing or deployment phases. The development and security teams can work together to identify potential vulnerabilities and address them before they become critical issues.
Some ways you can do this include:
- Include security team members to give input on non-security requirements
- Create threat models for new features and applications
- Invite security team members to participate in the threat modeling process
To ensure a more secure application and promote collaboration, involving the security team in the threat modeling process is crucial. In cases where the security team is unable to support every development team, implementing security champion programs can help ensure that the security team's objectives are represented during the design and development stages.
Implement Thorough Code Reviews
Implement a code review process to identify security vulnerabilities in applications. A code review aims to identify and correct issues in the code, improve code quality, and ensure that the code meets the project's requirements and follows best practices.
Read More: How to Improve Your Code Reviews
AppSec Pillar #2: Technology
The technology pillar refers to the security controls used to protect applications. There will always be new products and technologies being introduced to the market, so it's essential to understand the core needs for technology in application security.
Let's review how you can support the Technology Pillar of Application Security:
Code Scanning Tools
Code Scanning Tools, or Source Code Analysis Tools, are programs designed to test and analyze code to identify bugs and vulnerabilities before the computer program or application gets pushed live.
There are three types of Code Scanning Tools based on the type of scanning the tools are performing.
- Static Application Security Testing (SAST) - designed to analyze the source code of an application and spot potential issues in the early development stages
- Dynamic Application Security Testing (DAST) - examine a running web application from outside, simulating an actual attack just like a penetration test
- Interactive Application Security Testing (IAST) - analyze the source code of the web application while it is running to identify more vulnerabilities with a lower rate of false positives
Read More: How Code Scanning Tools Are Letting You Down
Integrated Development Environment
An Integrated Development Environment (IDE) is a software application that helps software developers write, debug, test, and deploy software. Essentially, it’s a tool that provides guide rails for developing applications.
As you write code within the IDE, the program can assist by providing syntax highlighting, auto-completion, and debugging tools. These types of features can help developers write code faster and more securely – it can also be used as a learning tool.
Just like most technology, it should be used as a tool and not as a substitute for the other AppSec pillars. These tools need human intervention to ensure they are programmed properly and working effectively.
Intrusion Detection Systems
An intrusion detection system is a software application that monitors a network for malicious activity or policy violations.
There are two main types of IDS:
- Network-based IDS (NIDS): NIDS monitor network traffic for suspicious activity. They are typically deployed at network choke points like firewalls and routers.
- Host-based IDS (HIDS): HIDS monitor system activity for suspicious activity. They are typically deployed on servers and workstations.
While intrusion detection systems are beneficial for application security, they are only as effective as the team programming them; this is why all three pillars are needed.
AppSec Pillar #3: People
Most organizations overlook this important pillar, they invest in the latest technology and implement strict processes, but your first two pillars are only as strong as your People pillar.
This pillar is all about managing Human Risk.
Human risk is the potential threat posed by human behavior to an organization, including the actions and behaviors of employees, contractors, and partners with access to the organization's systems, data, and information.
Examples of human risks include:
- Insider Threats
- Social Engineering Attacks
- Negligence or Human Error
Let's review how you can support the People Pillar of Application Security:
Security Awareness Training
One of the most effective ways to manage human risk in application security is to provide security awareness training to employees and contractors. This training should cover topics such as:
- Password hygiene
- Phishing prevention
- Social media oversharing
Organizations can reduce the risk of social engineering attacks, unintentional data disclosure, and other human-related security incidents by educating employees on these topics.
Secure Coding Training
Provide employees with training on security risks and best practices. Secure coding training aims to create software designed with security in mind rather than trying to patch vulnerabilities after they have been discovered.
Secure coding training typically covers topics such as common software vulnerabilities, secure coding best practices, and how to use security tools and techniques to find and fix vulnerabilities in software. By providing developers with secure coding training, organizations can reduce the risk of data breaches and other security incidents caused by vulnerable software.
Read More: What Is Secure Coding Training?
Access Control
Implement access control policies and procedures to ensure that employees only have access to the data and systems they need to do their jobs. For example, organizations should limit access to sensitive data and systems only to employees who require it to perform their job functions.
This can include measures such as:
- Role-based access control
- Two-factor authentication
- Least privilege access
What's Holding Up Your Application's Security?
Application security is a complex and ever-evolving field. However, organizations can significantly reduce the risk of application attacks by focusing on the three pillars of people, process, and technology. Contact our team today to learn how to build an application security program for your organization.


